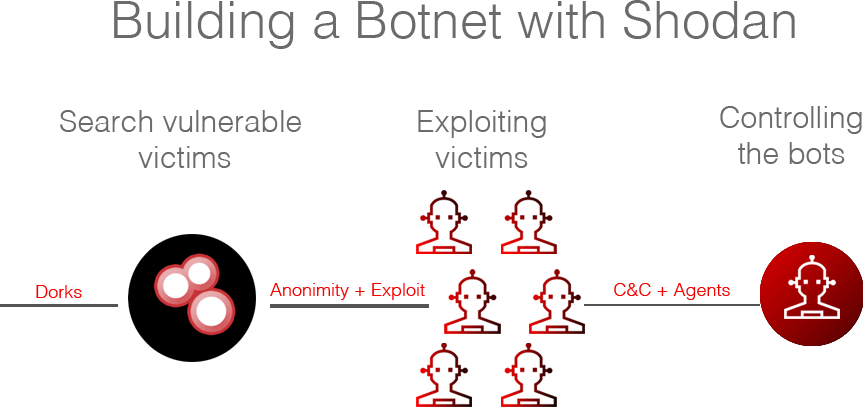
Building a botnet with Shodan

What is a Botnet?
According to Akami, a botnet is composed of a number of Internet-connected devices, like computers or IoT devices, each of which is running one or more bots. Botnet owners control them using command and control (C&C) software to perform a variety of (typically malicious) activities that require large-scale automation. These include:
- Distributed denial-of-service (DDoS) attacks that cause unplanned application downtime
- Validating lists of leaked credentials (credential-stuffing attacks) leading to account takeovers
- Web application attacks to steal data
- Providing an attacker access to a device and its connection to a network
What is Shodan?

Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of filters. Some have also described it as a search engine of service banners, which are metadata that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the server.
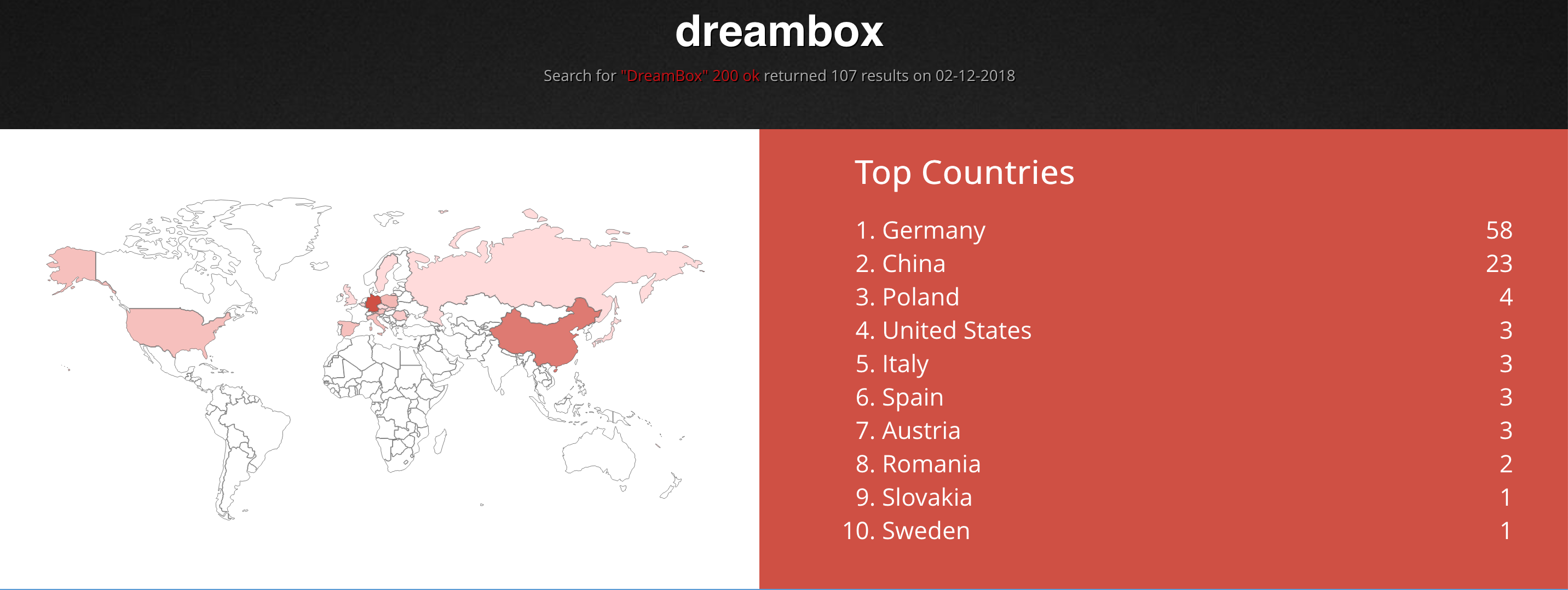
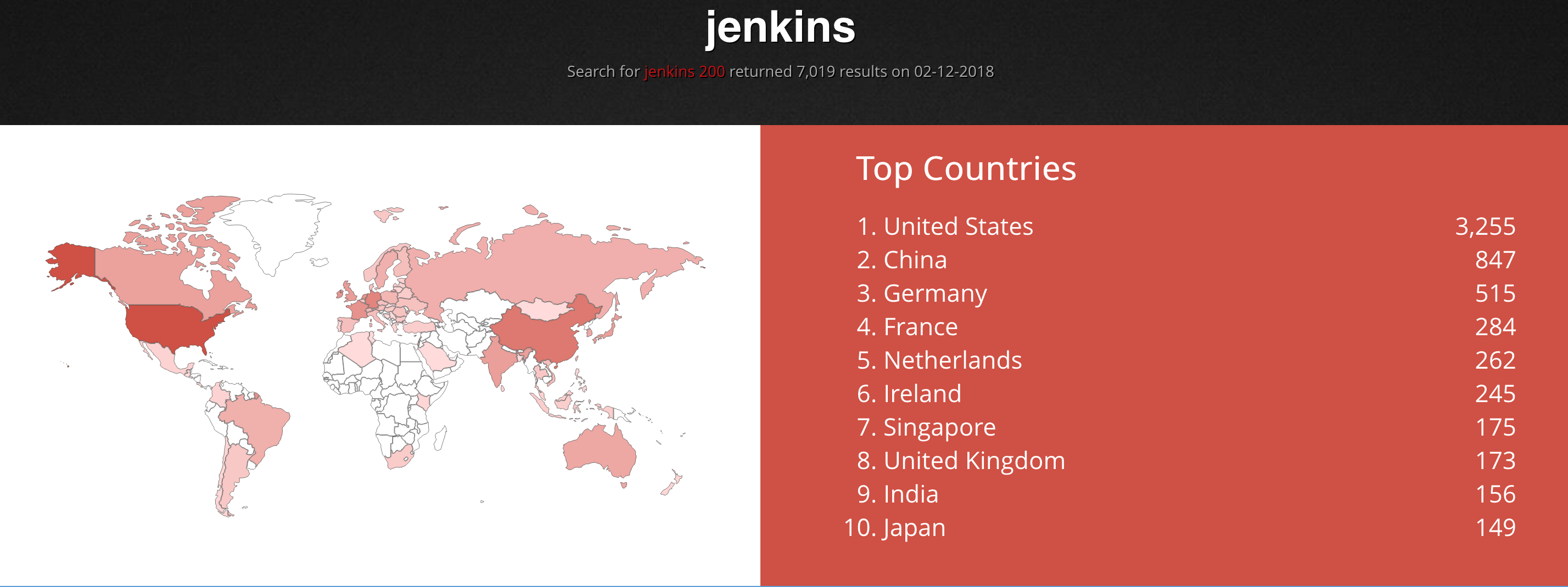
Therefore, Shodan allows in an easy way the discovery of potentially vulnerable servers, devices, routers, etc.
How to create a botnet?
- 1 Identifying vulnerable servers
- 2 Anonymizing the connection
- 3 Infecting the systems and controlling the bots
1. Identifying vulnerable servers
A dork is a query that with the correct searchwords, could identify a vulnerable server. For example, searching shodan dork in Twitter could help to identify potential entry points.
For example:
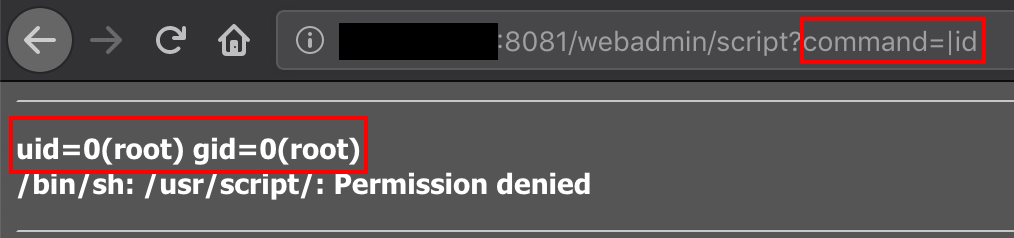
- authentication disabled port:445 : SMB Servers listing some folders. It could allow to read arbitrary data.
- Enable and Telnet passwords are configured : Strange banners that give information on headers. Maybe they are
honeypots. - “authentication disabled” port:5900,5901 : VNC server without authentication. It includes screenshots of the server.
- port:”3389”: RDP servers. It includes screenshots of the server.
2. Anonymizing the connection
It is very important not to use the current public IP leased by the ISP to prevent any possible identificacion. A good way to try to navigate anonymously is by using TOR. It is not enough to download TOR browser, because all reamining connections could leak our public IP. I propose two ways to retrieve anonymity:
2.1 TOR + Torsocks

Install a TOR proxy server locally to route all traffic through TOR. More info (left pane)
Install Torsocks. Torsocks is a library to allow transparent SOCKS proxying. It wraps the normal connect() function. When a connection is attempted, it consults the configuration file and determines if the IP address specified is local. If it is not, the library redirects the connection to a SOCKS server specified in the configuration file. It then negotiates that connection with the SOCKS server and passes the connection back to the calling program. It also ensures DNS queries are handled correctly and explicitly blocks all UDP traffic from the application in question.
After installing both, we could check the following.
- Tor proxy Server is running
tor
Dec 02 13:14:22.147 [notice] Tor 0.3.1.9 (git-727d3f1b5e6eeda7) running on Darwin with Libevent 2.1.8-stable, OpenSSL 1.0.2p, Zlib 1.2.11, Liblzma N/A, and Libzstd N/A.
Dec 02 13:14:22.147 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://www.torproject.org/download/download#warning
Dec 02 13:14:22.148 [notice] Read configuration file "/usr/local/etc/tor/torrc".
Dec 02 13:14:22.151 [notice] Opening Socks listener on 127.0.0.1:9050
Dec 02 13:14:22.151 [notice] Opening Control listener on 127.0.0.1:9051
Dec 02 13:14:22.000 [notice] Parsing GEOIP IPv4 file /usr/local/Cellar/tor/0.3.1.9/share/tor/geoip.
Dec 02 13:14:22.000 [notice] Parsing GEOIP IPv6 file /usr/local/Cellar/tor/0.3.1.9/share/tor/geoip6.
Dec 02 13:14:22.000 [notice] Bootstrapped 0%: Starting
Dec 02 13:14:22.000 [notice] Starting with guard context "default"
Dec 02 13:14:22.000 [notice] Bootstrapped 80%: Connecting to the Tor network
Dec 02 13:14:23.000 [notice] Bootstrapped 85%: Finishing handshake with first hop
Dec 02 13:14:23.000 [notice] Bootstrapped 90%: Establishing a Tor circuit
Dec 02 13:14:24.000 [notice] Tor has successfully opened a circuit. Looks like client functionality is working.
Dec 02 13:14:24.000 [notice] Bootstrapped 100%: Done
- Command shells programms are navigating anonymously
Command shells programms sould be run with the following syntax: torsocks <program> to force using torsocks. Some folders are protected from LD_PRELOAD, the best solution is to copy the binary locally and to execute like the following video:
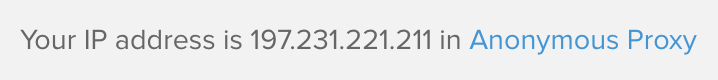
DNS leaks could be checked in https://www.dnsleaktest.com/ to ensure that anonymity works correctly.
2.2 Whonix

Whonix is a desktop operating system designed for advanced security and privacy. Whonix mitigates the threat of common attack vectors while maintaining usability. Online anonymity is realized via fail-safe, automatic, and desktop-wide use of the Tor network. A heavily reconfigured Debian base is run inside multiple virtual machines, providing a substantial layer of protection from malware and IP address leaks. Commonly used applications are pre-installed and safely pre-configured for immediate use. The user is not jeopardized by installing additional applications or personalizing the desktop. Whonix is under active development and is the only operating system designed to be run inside a VM and paired with Tor.
3. Infecting systems and controlling the bots
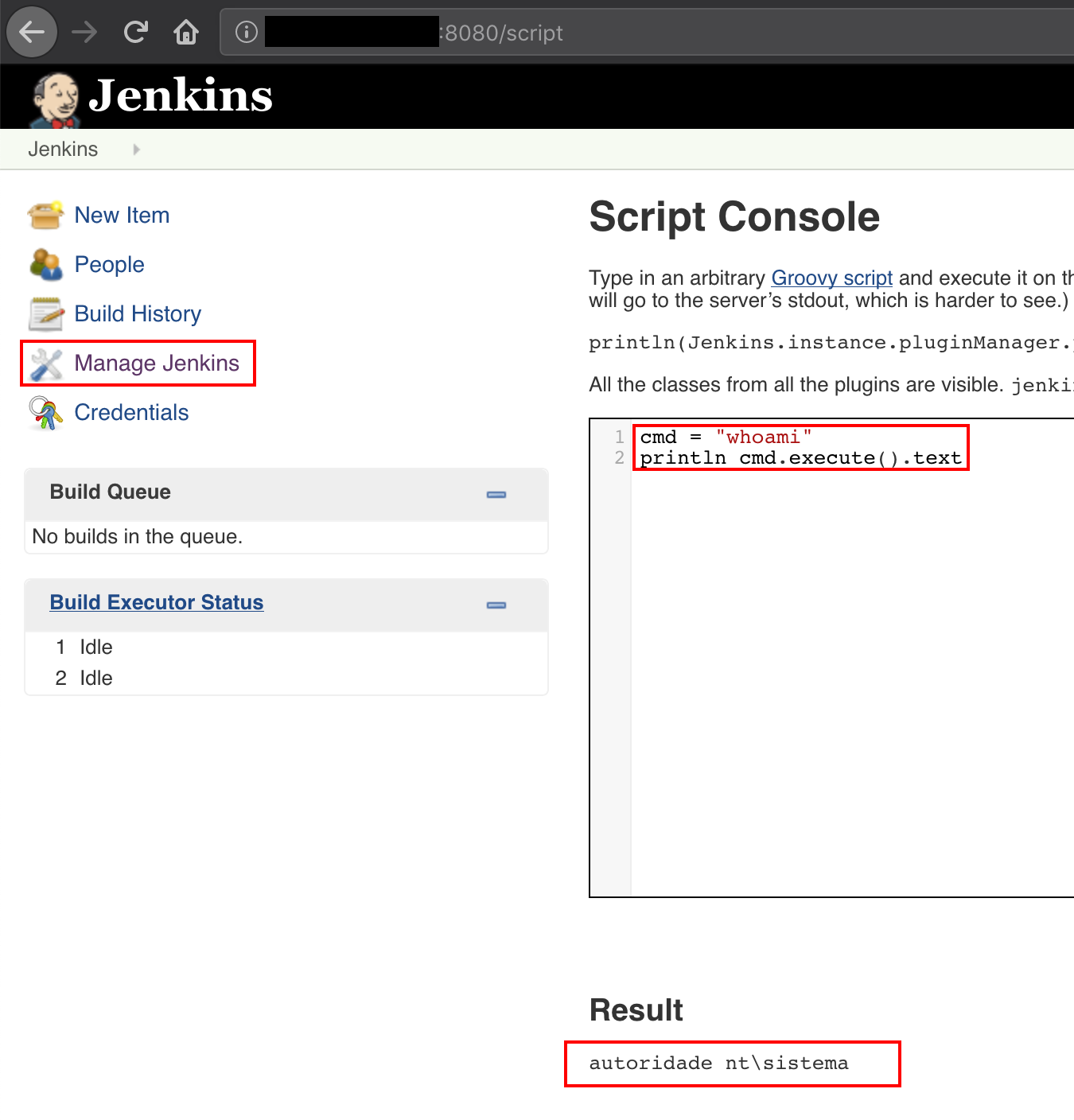
Once a secure connection has been established, the final part is to identify potentional victims. Victims are required to have a Remote Code Execution vulnerability. For example.
The final step is to infect with an agent of a Command & Control, for example Merlin.
All the process could be automated using Shodan's API and the desired exploit in each scenario.
Conclusions
It is very important to identify what services we have exposed to the internet. We should check the configuration of our Router and Firewall, and search our public IP in webpages like Shodan or Censys. If we need to have a service opened, establish a strong authentication and update to the last version, trying to patch all detected vulnerabilities. It is a better practice to establish a VPN to reach these services in a safer way.